認識加密攻擊及勒索軟件的未來
Meet The Cryptoworm, The Future of Ransomware
Threat Post 2016-04-15 11:30:00https://threatpost.com/meet-the-cryptoworm-the-future-of-ransomware/117330/
Ransomware is evolving and soon will share the same deadly efficiencies as notorious worms of the past, such as Conficker and SQL Slammer. In fact, according to security researchers at Cisco Talos, today’s newest ransomware, SamSam, is a harbinger of a new wave of more malicious, tenacious and costly ransomware to come.
“Ransomware authors are always looking for bigger payouts and to further their reach,” said Joe Marshall, security research manager with Cisco Talos. “We believe ransomware authors are going to look to past successful campaigns when they look to cast a wider net in the future.” s Trend Micro™ Security, Smart Protection Suites, and Worry-Free™ Business Security can protect users and businesses from this threat by detecting malicious files, and email messages as well as blocking all related malicious URLs.
Marshall predicts that today’s ransomware authors have begun to shift strategy away from “spray and pray” mentality where ransomware payloads are delivered indiscriminately via exploit kits or mass phishing campaigns. He said, the age of self-propagating ransomware, or “cryptoworms”, is right around the corner.
“This new ransomware is a mix of old and new. It has adopted self-propagating properties of worms and malware of the past. And it has new tricks when it comes to traversing corporate networks laterally to find the most vulnerable targets,” said Marshall, a co-author of the Cisco Talos report “Ransomware: Past, Present and Future” released Tuesday.
Marshall said this next ransomware blends the best of decade-old infection techniques used with Conficker and SQL Slammer worms with modern day network intrusion smarts.
Conficker was the golden boy of malware in 2008. It infected millions of home and business computers in 190 countries at the time, and remained a potent threat for years following its initial outbreak as malware authors cooked up multiple variants. SQL Slammer dates back to 2003 and was so pernicious it was blamed for slowing internet traffic down for a day in some countries and infecting PCs at lightning speed.
“We are going to see repurposing of older persistent threats,” said Craig Williams, senior technical leader for Cisco Talos. “A lot of people would assume that in order for the next generation of ransomware to be effective that they would need a new network vulnerability. The reality is, that’s not the case. These attackers can take any off the shelf network vulnerability and make a worm out it.”
Cisco Talos said that the SamSam, first spotted last month, targets unpatched server vulnerabilities and is a close cousin to a computer worms mimicking the way they can penetrate an operating system, spread malicious code and traverse across a network. To be clear, SamSam is not entirely self-sufficient. “But it does exhibit some of the behaviors of a successful worm – rapid propagation, payload delivery (ransomware), and crippling recovery efforts,” writes the Cisco Talos team in its report.
Cisco Talos researchers say future ransomware will build off of SamSam’s core. Newer versions will have more autonomy and will deliberately target enterprise network vulnerabilities. That attack framework for future ransomware infections might include targeting unprotected executable files, searching a network for attached storage drives to copy itself to, attempts to exploit authentication weaknesses and ensuring ransomware used minimum system resources to help avoid detection, Cisco Talos writes.
Right now, SamSam’s attack vector du jour is JBoss, and vulnerabilities in the Java web application framework, Marshall said. “Its next attack vector is anyone’s guess,” he said.
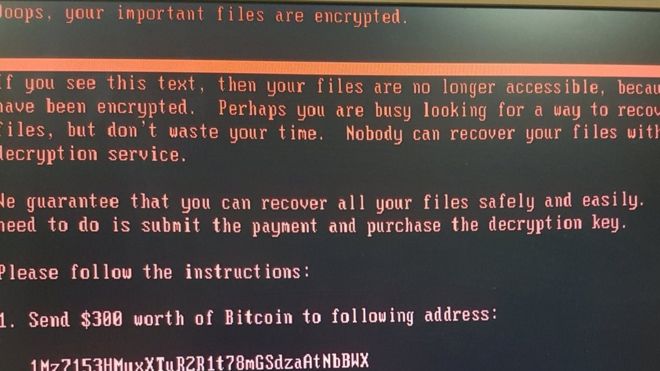
Cisco Talos predicts this type of cryptoworm could see massive scale. And a successful campaign, researchers say, will jack up the price of ransomware decryption keys. Right now ransomware authors are demanding between a 0.5 ($220) and 1 ($420) Bitcoins per infected machine. In the future, the price is expected to rise significantly, Williams said.
For companies, the only way to effectively neutralize the threat is to make sure they have up-to-date backups and a flawless backup restoration protocol.
“The cryptoworm’s Achilles Heel is a reliable backup, so you don’t have to be extorted,” Williams said.
Clearly, the best way to prevent an attack is before it starts. Cisco Talos recommends DMZ hardening, or boosting security on a company’s perimeter and public-facing network. “For too long, critical security controls and best practice for enterprise network security has been publicly praised and privately ignored,” Cisco Talos chides. “If enterprises don’t start making strides towards defensible architecture today, massive ransoms may end up getting paid tomorrow,” Cisco Talos writes.